Leaving a stable cybersecurity job to start your own firm? That’s a bold and exciting move!
With cyber threats at an all-time high, businesses of all sizes are desperate for protection, creating huge opportunities for new cybersecurity service providers.
But even with technical expertise, diving in without a clear plan can lead to costly mistakes. A strong business plan helps you stay focused, define your services, set smart goals, and build client trust from day one.
Not sure how to get started?
Don’t worry. This cybersecurity business plan template walks you through it, step by step.
Why is a cybersecurity business plan important?
When starting a cybersecurity company, creating a solid business plan is one of the most important steps. It helps you define the services you'll offer, the clients you want to target, and how your business will generate revenue.
Think of it as your roadmap; it keeps you focused and avoids decisions based on guesswork or missed opportunities.
Further, a plan keeps you aligned as the business grows. Without it, it’s easy to lose direction or make choices that don’t fit your goals.
Your plan doesn’t have to be perfect. What matters is that it gives you structure and direction. Treat it as a working document—something you update as you grow and adjust to new challenges.
A well-prepared plan shows that you've thought things through. It reflects a clear understanding of your market, your risks, and how you’ll run your operations. In short, it shows you're serious.
How to create a strong cybersecurity business plan?
Creating a cybersecurity business plan may seem complex, but breaking it into clear steps makes the process easier to manage.
Here are the key sections your plan should include, along with practical tips for writing each one:
1. Executive Summary
The executive summary is the elevator pitch for your cybersecurity business. Though it appears first, it’s often written last, after you’ve detailed each section of your plan.
This summary gives readers a concise overview of your entire plan, highlighting the most important points.
Here are the key components to include in your executive summary:
- Business overview: Briefly introduce your cybersecurity company: its name, location, and what services you offer.
- Market opportunity: Summarize your market research. Who needs your services and why? Highlight a key stat or trend.
- Services & USP: Outline the core cybersecurity services you’ll provide and what makes your approach unique. Emphasize your unique value proposition. Why will clients choose you over others?
- Financial highlights: Provide a snapshot of your financial projections. Mention expected revenue streams and when you anticipate profitability.
- Milestones & goals: Optionally, note one or two big goals. This shows you have an eye on growth.
Keep the tone confident and factual. By the end of this section, even a busy reader should grasp what your business is and why it’ll succeed.
2. Company Description
Now it’s time to describe your cybersecurity company in detail!
The company description covers the foundational information about your business – who you are, what you do, and why you do it. Think of it as the “who/what/why” of your company’s story.
Key elements to include in your company overview:
- State your business name and location. Mention when and by whom the company was founded.
- Specify your business structure. This is important for legal and tax purposes, which can instill confidence that you’ve set up properly.
- Share a short, inspiring mission statement that captures your purpose. What core mission drives your cybersecurity firm?
- Briefly mention your long-term vision. Where do you see the business in 5 years? Perhaps expanding into cloud security products or becoming a regional leader in cyber defense.
- Introduce the founders or key team members. If multiple founders, note who they are and what expertise they bring. Also mention the ownership structure, if relevant.
If you’ve already launched, provide a brief history. When did you start operations, and what progress have you made? This could include early client projects, beta tests, or any awards/recognition. If you’re pre-launch, you can skip this or mention what inspired you to start the business.
Overall, this section sets the stage for the rest of your plan by establishing your identity and purpose. Keep it concise but meaningful—you can delve into specifics later on.
By the end of the company overview, the reader should have a clear picture of what your business is and aims to achieve.
3. Market Research
The market analysis section shows that you truly understand the cybersecurity field and the people you're aiming to serve. It’s a key part of your plan, especially for investors or partners who want to see that you’ve done your research on industry trends, demand, and competition.
Here’s what to include in this section:
Industry Overview
Describe the current state of the cybersecurity industry. Is it growing? Mention the high demand for cybersecurity services globally and in your region.
Highlight any relevant regulations or standards that drive the need for security compliance.
Target Market
Identify your target customers and their needs. Who exactly will you serve? Perhaps it’s small healthcare clinics concerned about patient data, or mid-sized e-commerce companies needing PCI compliance.
Explain the pain points these customers face. By pinpointing the problem, you validate the need for your services.
Market Size & Growth
Include numbers where possible to show the size of your target market. Estimate how many businesses in your area or niche are likely to need cybersecurity services.
If you have reliable data or statistics, include them. You can also mention local trends like a rise in tech startups or new cybersecurity regulations, which could increase demand for your services.
Competitive Landscape
Analyze the competition. Who else is offering similar services in your market? This includes direct competitors and indirect competitors.
Discuss 3-5 key competitors: their size, services, and what differentiates them. It’s helpful to present this as a short comparison. Identify what competitive advantage you have.
Market Opportunity
Based on the above, underscore the opportunity for your business. This is essentially your “Why now?” and “Why us?” moment. You might also mention expected market growth in your niche.
In addition, a quick SWOT analysis can be a handy tool within market analysis. Consider including a SWOT matrix to summarize your internal strengths/weaknesses and external opportunities/threats.
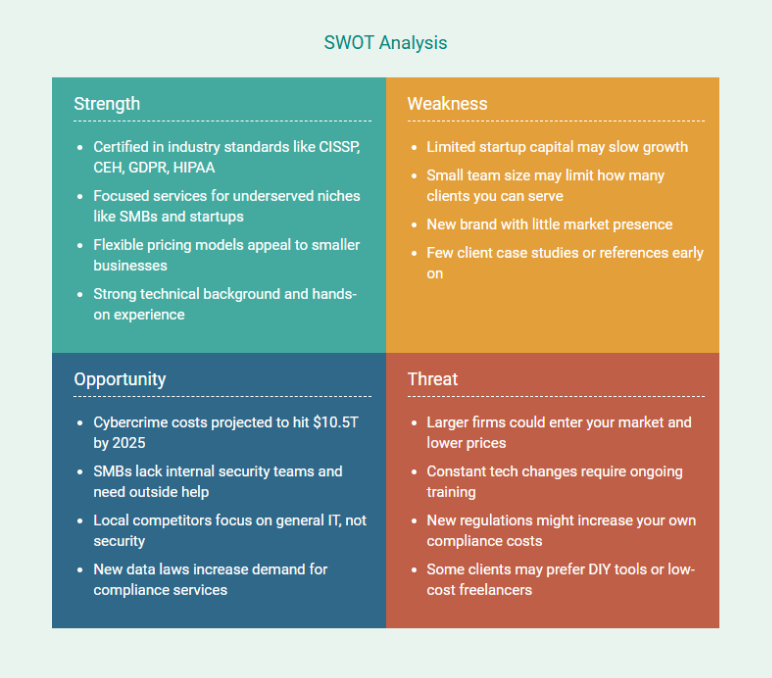
In short, the market analysis should convince the reader that there’s a real need for your services and that you understand the playing field. Use data and real examples where possible, and cite credible sources for any statistics or claims.
A well-researched market analysis section not only guides your strategy but also builds confidence that your cybersecurity startup is grounded in reality.
4. Service Offerings
In this section, list and describe the cybersecurity services you‘ll offer to customers. Be clear about what you’re providing and how it solves the problems outlined in your market analysis.
You're not just offering “cybersecurity” in general; explain the specific solutions you deliver and how each one helps your target market.
Common services for a cybersecurity firm might include:
- Vulnerability assessments & penetration testing: Testing client systems for weaknesses and simulating attacks to identify vulnerabilities.
- Security audits & compliance consulting: Reviewing a company’s security policies and infrastructure to ensure they meet standards and regulations (HIPAA, GDPR, ISO 27001, etc.).
- Managed security monitoring: Ongoing monitoring of networks and systems to detect and respond to threats in real time.
- Incident response & remediation: On-call services to handle security breaches or incidents.
- Cybersecurity training & awareness: Educating client employees on security best practices. This is a high-demand service as human error is a leading cause of breaches.
- Consulting for security architecture: Designing and implementing secure network architecture or cloud security for clients starting new projects or expanding.
For each service or category, write a brief description focusing on the benefit to the client. It’s often effective to bullet-point the services for clarity. Ensure the list is symmetrical and parallel.
Make sure your service list matches what your target customers need. Every service should tie back to a problem you identified earlier—that’s what makes your business plan focused and convincing.
5. Marketing and Sales Strategy
You might have strong services in place, but that’s only part of it. The real question is, how do you plan to get people to notice you, and once they do, why would they stay? That’s where marketing and sales come in.
In cybersecurity, people won’t just sign up because you say you're good. They need to feel they can trust you. So, your message should show them that clearly and confidently.
Here’s what to include in this section:
Branding & positioning: How will you position your cybersecurity brand? Think about your brand message and tone. Mention plans for a professional website showcasing thought leadership to build credibility.
Sales strategy & process: Explain how a lead becomes a customer. Who will handle sales? You or a salesperson? Outline your sales funnel. Note your expected sales cycle—cybersecurity services often have longer cycles due to trust and budget concerns.
Pricing strategy: Summarize how you price services. Will you charge hourly, project-based, or offer monthly subscriptions? Ensure pricing is competitive but sustainable. If you offer tiered packages, mention it.
Customer retention: Keeping clients is as important as finding them. Briefly mention strategies like regular reporting, quarterly review meetings, and 24/7 support for incidents. Satisfied customers may buy more and refer others.
Overall, this section should convince the reader that you have a concrete plan to get clients and generate revenue.
6. Operations Plan
The operations plan explains the day-to-day workflow and infrastructure of your cybersecurity business. Essentially, how will you deliver your services efficiently and effectively?
This section is about demonstrating that you have the processes, tools, and operational strategy to back up your marketing promises.
To draft this section effectively, consider including these operational aspects:
- Service delivery process
- Operational workflow & scheduling
- Quality assurance
- Suppliers and partners
- Location & facilities
- Future operations plan
Keep the operations plan straightforward and realistic. You want to instill confidence that you can deliver what you promise to clients daily. Investors often appreciate seeing that you have thought about the nitty-gritty details—it means fewer unpleasant surprises down the road.
7. Management Team
This management team section explains who’s running the business and why they’re qualified to make it succeed.
Start by outlining your team’s structure and each person’s role, even if it’s just two people. If you plan to grow, mention key future hires like a security analyst or sales manager, along with what they’ll do.
Add short bios highlighting relevant experience, certifications, and achievements. If your team isn’t complete, be transparent about what’s missing and how you’ll fill those roles.
Show how your team—or you, if you’re solo—can handle the challenges covered earlier. Mention any mentors or advisors supporting you.
Adding a simple org chart can help readers quickly understand how the team works together.
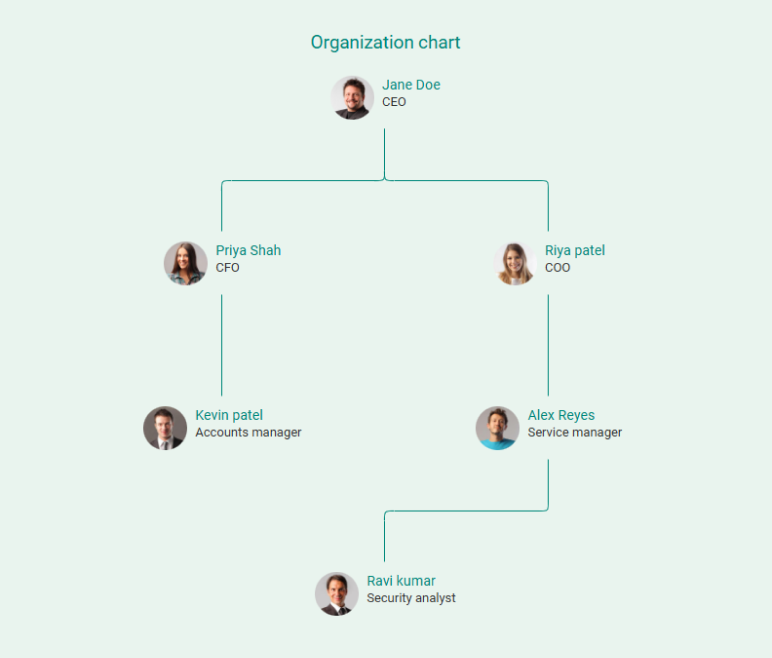
By the end of this section, readers should feel confident that the business has the leadership and skills to execute the plan.
8. Financial Plan
The financial plan outlines how your cybersecurity business will generate revenue, manage expenses, and grow profitably. It includes projections like income, cash flow, and break-even analysis.
Even if you're not a finance expert, this section shows that you've carefully considered how the business will sustain itself.
If you're seeking funding, it's one of the most important parts—investors will study these numbers to decide if your business is a good investment.
Your financial plan should include forecasts and statements such as:
- Startup costs: Include all one-time expenses like equipment, software, licenses, and initial marketing. These are the costs required to get your cybersecurity business off the ground.
- Revenue projections: Estimate how much income your business will generate over the next 3–5 years, based on pricing and expected clients.
- Profit & loss: Forecast your annual profits or losses by comparing projected income against your operating expenses.
- Cash flow: Show when money will come in and go out each month, and how you’ll handle any periods of negative cash flow.
- Balance sheet: Summarize yearly assets, liabilities, and owner equity to reflect the financial position of your business.
- Use of funds: If seeking funding, clearly state how much you need and explain how each portion will be used.
The financial plan might seem overwhelming, but it’s a critical part of your business plan. Keep it realistic; being slightly conservative is better than overpromising and missing targets.
Make sure your numbers are accurate, match the rest of your plan, and double-check all calculations. You can also use financial forecasting tools to help build more reliable projections.
Download a free cybersecurity business plan template
So, are you all set to craft your cybersecurity business plan from scratch? But need more assistance with that? Well, look no further. Here, you can download a free cybersecurity business plan template (PDF) to help you get started.
This template covers all the key sections of a strong cybersecurity business plan. It includes real-world examples and is easy to adapt to your specific goals, whether you're launching a consulting service, managed security operation, or compliance-focused firm.
Get help writing your plan
After reading the comprehensive guide, you now have a better understanding of how to create a cybersecurity business plan in 8 easy steps.
But if you ever feel stuck or need expert advice along the way, don’t hesitate to reach out to professional business plan consultants. They’ll help you polish your plan and ensure it’s ready to impress investors.
So, why wait? Start planning today!
Frequently Asked Questions
Do I really need a formal business plan for a cybersecurity startup?
Yes, even if you're going solo, writing a business plan keeps things from getting messy. It helps you figure out who you're trying to help, what exactly you're offering, and how you're going to make it all work. If you're hoping to raise money or work with partners down the line, you'll definitely need one. More than anything, it forces you to slow down and think before jumping in, and that’s always worth it.
What are the typical startup costs for a cybersecurity consulting business?
The typical startup costs cybersecurity consulting business can vary widely based on the scale and setup.
Here’s a breakdown of key cost areas:
Typical startup cost range:
- $5,000–$15,000 for solo consultants
- $100,000–$350,000 for larger-scale operations or early hiring
How can a new cybersecurity company get its first clients?
Getting your first clients is often about networking and trust. Start by reaching out to people you already know, friends, former colleagues, or local business contacts. Offer a free or low-cost security assessment to show value and build credibility. Sharing practical tips on LinkedIn or relevant online forums can also position you as a knowledgeable and helpful expert in the field.
What services should a small cybersecurity startup focus on offering?
A small cybersecurity startup should start with high-demand, manageable services like vulnerability assessments, firewall setup, and employee security training. As it grows, it can expand into areas like penetration testing and incident response, focusing on quality and client needs.
Do I need any specific certifications or licenses to start a cybersecurity business?
You don’t need special licenses beyond registering your business, but having certifications can make a big difference. Recommended certifications:
- CISSP(Certified Information Systems Security Professional)
- CEH(Certified Ethical Hacker)
- OSCP(Offensive Security Certified Professional)
- CISM(Certified Information Security Manager)
These will help boost credibility and meet client expectations. Also, ensure compliance with local laws and get proper business insurance.

